Single sign-on vs multi-factor authentication often confuses people because both improve security but work differently. SSO lets you access multiple applications with one set of credentials, while MFA requires you to verify your identity through multiple methods before granting access. Think of SSO as a master key that opens several doors at once, and MFA as a security checkpoint that asks for multiple forms of ID. Neither replaces the other. They serve distinct purposes in protecting your digital resources.
This article breaks down the key differences between these authentication methods and shows you how they complement each other. You’ll learn when to use each approach, what makes them different, and why combining both creates stronger security without frustrating your users. We’ll clear up common misconceptions and give you practical guidance for building an authentication strategy that works for your organization. By the end, you’ll understand exactly how these technologies fit into your security plan.
Why understanding authentication protocols is vital
Your organization’s authentication strategy directly affects both security and productivity. When you don’t grasp how different protocols work, you make decisions that either expose your systems to breaches or frustrate your users so much they find workarounds. Poor authentication choices cost businesses millions in data breaches and lost productivity every year. Understanding the fundamentals of single sign on vs multi factor authentication helps you build defenses that actually work instead of creating security theater that looks good on paper but fails in practice.
Security risks from poor authentication
Weak authentication opens doors for attackers to steal credentials, access sensitive data, and move laterally through your network. Relying solely on passwords leaves you vulnerable because users reuse them across multiple platforms, making one breach a gateway to everything. You face increased risk when you implement security measures without understanding their purpose or limitations. Combining incompatible authentication methods can create gaps that sophisticated attackers exploit. Your security is only as strong as your weakest authentication point, and misunderstanding protocols guarantees weak spots in your defenses.
Authentication failures account for a significant portion of successful cyberattacks, making proper implementation critical for any security strategy.
Business impact of authentication choices
The authentication methods you choose affect how quickly your employees work and how much IT support they need. Complex authentication processes slow down workflows and lead to support tickets that drain resources. When you force employees through too many steps, they abandon proper channels and share credentials or store passwords insecurely. Balancing security with usability requires understanding what each protocol actually does. Your customers also feel the impact when authentication creates friction during purchases or service access. Smart authentication choices reduce overhead costs while improving both security and user satisfaction. You need this knowledge to make decisions that protect your business without hampering operations.
How to differentiate between SSO and MFA
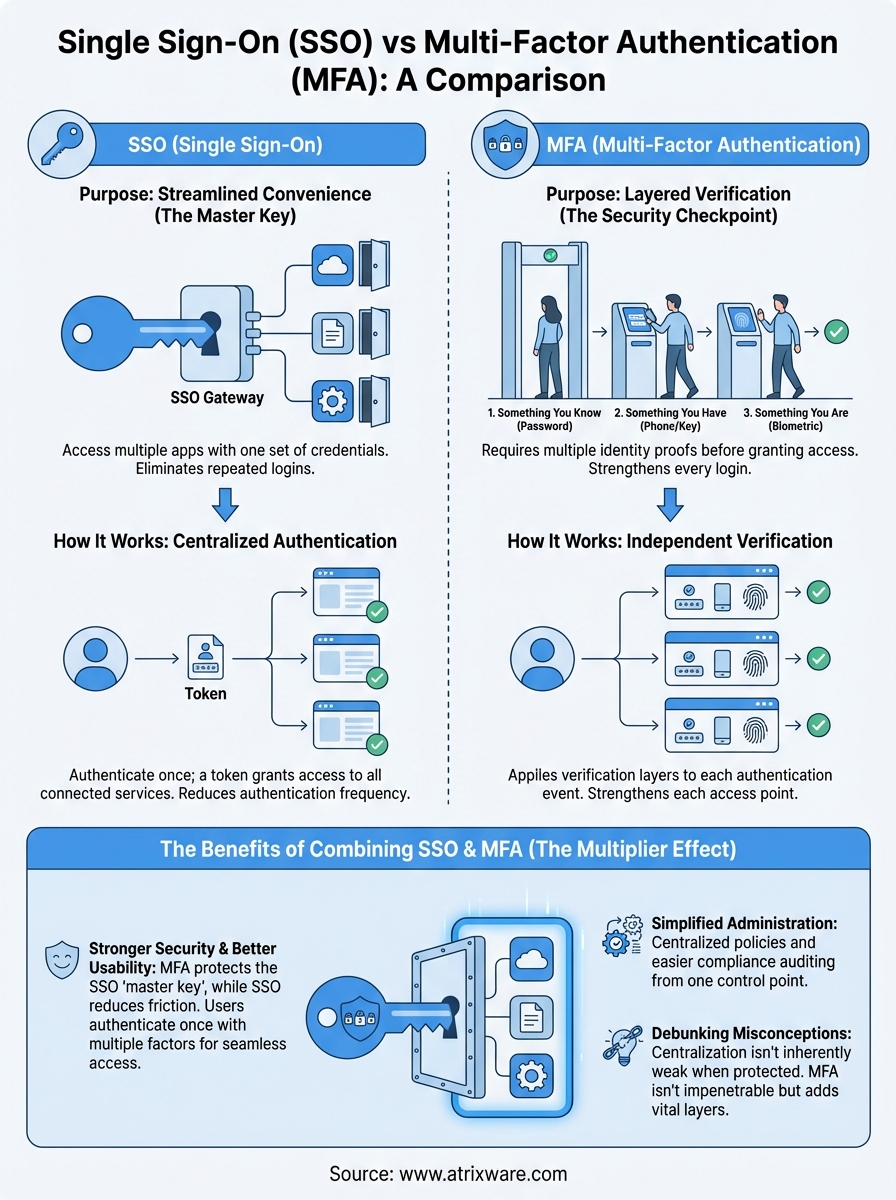
The core difference between single sign on vs multi factor authentication comes down to their purpose. SSO eliminates the need to log in multiple times by letting you authenticate once and access all connected applications. MFA adds verification layers to confirm you are who you claim to be before granting access. SSO focuses on convenience and streamlining access, while MFA prioritizes security through additional proof of identity. You can think of SSO as reducing authentication friction and MFA as increasing authentication rigor. They solve different problems in your security architecture.

What SSO actually does
SSO creates a single authentication gateway that grants access to multiple applications after one login. When you sign in through an SSO provider, it generates a token that other applications recognize, letting you move between systems without entering credentials again. Your identity verification happens once at the SSO provider level, and that provider then vouches for you to all connected services. This reduces password fatigue and helps IT teams manage access centrally. You experience fewer login screens and spend less time retrieving forgotten passwords.
SSO doesn’t strengthen authentication itself but consolidates it into a single point, making that point critical to protect.
What MFA actually does
MFA requires you to provide multiple forms of verification before allowing access to any system. These verification factors typically include something you know (password), something you have (phone or security key), and something you are (fingerprint or face scan). Each additional factor makes unauthorized access harder because attackers need more than stolen credentials. Your login process takes longer, but the security improvement is substantial. MFA works independently of how many systems you access, applying its verification requirements to each authentication event unless configured otherwise.
The benefits of combining SSO and MFA
Using SSO and MFA together creates a security framework that protects your systems without overwhelming users. When you implement both, SSO reduces authentication frequency while MFA strengthens each authentication event. This combination addresses the core weakness of SSO: if someone compromises your single sign-on credentials, they potentially access everything. MFA fixes this vulnerability by requiring additional verification factors that attackers typically don’t possess. You get streamlined access for legitimate users and robust protection against unauthorized access attempts.
Stronger security with better usability
The partnership between single sign on vs multi factor authentication eliminates the false choice between convenience and security. Your users authenticate once with multiple factors, then enjoy seamless access to all connected applications. This approach reduces password reuse across systems because users only need to remember one strong credential set. You maintain strict verification standards without forcing employees through repeated authentication screens that kill productivity. The result is fewer support tickets for password resets and lower risk of credential-based breaches.

Combining SSO with MFA creates a security multiplier effect where each technology compensates for the other’s limitations.
Simplified administration and compliance
Managing access becomes easier when you centralize authentication through SSO and enforce verification standards through MFA. You can apply consistent security policies across all applications from a single control point. This makes compliance auditing simpler because you track authentication events in one location rather than scattered across multiple systems. Your IT team spends less time managing individual application passwords and more time on strategic security initiatives.
Common misconceptions about access security
Many organizations make costly assumptions about authentication that undermine their security posture. These misconceptions lead to incomplete implementations where you deploy solutions without understanding their actual capabilities and limitations. When you believe myths about single sign on vs multi factor authentication, you either over-rely on one method or avoid implementing effective combinations. Understanding what these technologies can and cannot do helps you build realistic security expectations and avoid dangerous gaps in your defenses.
SSO weakens security by centralizing access
This misconception stems from viewing centralization as inherently risky rather than understanding that SSO simply consolidates authentication points. SSO itself doesn’t make systems less secure because security depends on how you protect that central access point. When you combine SSO with strong authentication methods like MFA, you create a more secure environment than scattered passwords across multiple systems. The real risk comes from protecting your SSO credentials with only a password, not from consolidation itself.
Centralized authentication becomes a strength when you protect it properly, not a weakness by default.
MFA guarantees complete protection
MFA significantly improves security but doesn’t create an impenetrable barrier against all attack methods. Sophisticated attackers use phishing techniques that capture MFA codes in real-time or exploit vulnerabilities in specific authentication factors. Your MFA implementation remains vulnerable if you choose weak second factors or fail to update authentication methods as attacks evolve. Security requires multiple defensive layers, not reliance on any single technology as a complete solution.
Final thoughts on digital security strategies
Your authentication strategy needs both single sign on vs multi factor authentication working together to achieve real security. Neither technology alone solves your access control challenges. SSO streamlines how your users navigate between applications, while MFA verifies their identity with multiple proof points. Combining these approaches creates a framework that protects your organization without creating unnecessary friction.
Start by evaluating your current authentication setup and identifying where vulnerabilities exist. Choose an LMS platform that supports modern authentication standards and integrates seamlessly with your existing security infrastructure. Test your organization’s readiness for implementing advanced security features to understand what authentication improvements would benefit your specific training environment.
Building effective digital security requires understanding the tools at your disposal and using them strategically. Your investment in proper authentication pays dividends through reduced breach risk, improved compliance, and better user experience.
